I recently gave a presentation to the Cultural Studies PhD program at George Mason University. That's the program where I earned my PhD, so it was an honor to come back and talk to my professors as well as some of the new students currently in the program.
I took the presentation as an opportunity to reflect on my academic career from my time at Mason (2005-2010) to my latest book project. I've modified it for this blog. Take a look at the abstract and, if piques your interest, feel free to read it! (It's a bit long.)
Abstract
In my time as a PhD student in GMU's Cultural Studies program, I learned that I must let my object of study tell me what methods to use to analyze it. I also learned not to merely interpret the object, but seek to change it. Since I chose to study what was then called "Web 2.0" and what I now call "corporate social media," I needed to bring Marxian political economy, science and technology studies, and software studies to bear on the object. And I began to examine the practices of activists who sought to make something better than corporate social media: alternative social media. Over a decade ago I began my adventures in alternative social media, chasing it through hacker collectives, cyberlibertarian organizations, and even onto the dark web. Through digital ethnography, close examinations of code, and hands-on experience running alternative social media, I developed an approach I call "critical reverse engineering." Here I present critical reverse engineering as a methodology for activist engagement with digital technologies. To illustrate this approach, I will draw on insights from my forthcoming book, Move Slowly and Build Bridges: Mastodon, the Fediverse, and the Struggle for Ethical Social Media (Oxford, 2025).
Introduction: Do we call it X or Twitter?
Is it X? Or is it Twitter?
Because I've heard media critics use both names, even well after Musk bought Twitter in 2022.
I hear media critics say, "X is out of control. It's full of disinformation and pornbots. Musk is slowly destroying it, indicating the fundamental problem of billionaires owning social media."
And then, I often hear those same media critics tell their readers and listeners, "Please follow me on Twitter."
It's "X" when you hate it and "Twitter" when you love it.
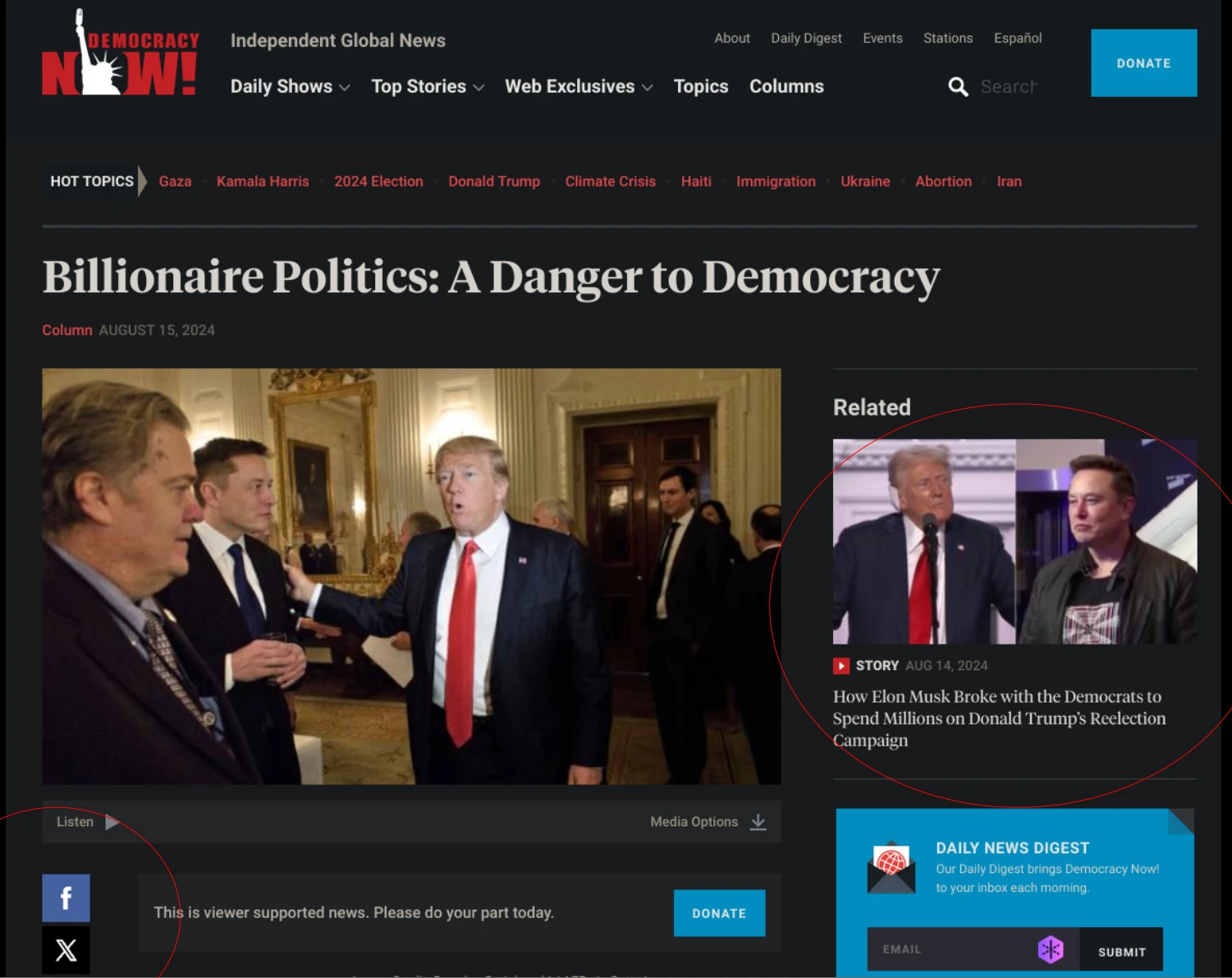
This screenshot of Democracy Now! doesn't quite illustrate my point, but it gets close. Here are stories about billionaire media owners -- including Elon Musk -- who run amok. But please do follow us on the very platforms we decry.
This encapsulates the contradictions of corporate social media: we may complain about them, about surveillance capitalism, exploitation of our sociality, algorithms that push content on us, about addiction.
And yet we also believe they are the only tool we have to speak up, to organize, or more humbly, to connect and share with our friends.
Leaving Corporate Social Media
In contrast, my career has largely been dedicated to the idea that we can and must leave corporate social media behind. That we can maintain their pleasures while effectively taking them over. For over a decade now, I've been talking to activists and technologists seeking to make something better than X or Facebook.
This presentation is a bit of a reflection on my academic career and how I came to study alternative social media. It starts with my time in Cultural Studies at Mason (2005-2010), then the period around the writing of my first book, Reverse Engineering Social Media a decade ago, and culminating in my current book, Move Slowly and Build Bridges, which should come out next year.
My plan for this is roughly chronological:
- Part 1: Cultural Studies and Web 2.0
- Part 2: Seeking Critical Reverse Engineers
- Part 3: Adventures in Alternative Social Media
- Part 4: New Critical Reverse Engineers on the Fediverse
Part 1: GMU Cultural Studies, Web 2.0 (2005 -- 2010)
Thinking back, what I learned during my time in the Cultural Studies PhD progam at Mason were two lessons:
- First, what does the object of study need you to do to understand it? How does the object demand particular methodologies?
- Second, "the point is to change it." That is, the point of our work is to make a better world.
Finding an Object: Web 2.0
First I needed an object of study.
I came to the object of my study during a class with GMU Cultural Studies professor Alison Landsberg. She said, "someone ought to take a look at Youtube," in her Visual Cultures class.
At the time, YouTube was making headlines because of its eye-popping sale to Google for \$1.65 billion USD.
Like many people, professor Landsberg was perhaps wondering how a relatively obscure website could be sold for such a sum. Prior to Google's purchase, YouTube was best known as a place where people either uploaded pirated videos or made "vlogs," personal, self-confessional video blogs (as well as "vlogs" that turned out to be fictional, yet compelling).
The users had made YouTube what it was -- contributing videos, commenting on them, building a culture. Were they getting a cut of the $1.65 billion?

The case of YouTube led me to what at the time was called Web 2.0, where, as Tim O'Reilly and John Batelle argued in 2004, users of digital technologies do the work of building businesses. Where users create data -- about the world, and about themselves -- that companies can harvest for new ideas and profit.
Were Youtube's users getting a cut, then? No. From a note I took around the time, I wrote "These companies ask us to build them, and then expect us to consume their products, without compensation beyond a 'richer' user experience."
And of course I wasn't the first to say this -- Tiziana Terranova had already theorized free labor in digital media, and many others had taken up that concept.
Now of course many people recognize what's going on, and call this "surveillance capitalism." It's an idea so recognizable that even the US Federal Trade Commission has just now noticed it happening!
Welcome to the party, FTC. We've been talking about this since the 2000s.
Methods: Marxian political economy, science and technology studies, and software studies
So my object became Web 2.0, or surveillance capitalism, or specifically what I now call corporate social media.
What methods could I bring to bear?
These are digital technologies and they involve communicative practices, and they are embedded deeply in capitalism. They rely upon user-generated content -- that is, freely given labor -- to produce valuable digital artifacts that attract attention.
The object spoke, and one thing it said to me was "use Marxian political economy to understand me." Marx's Grundrisse turned out to be valuable -- particularly as Stuart Hall] and Nick Dyer-Witheford had interpreted it.
The object also told me to use science and technology studies -- particularly conceptions of heterogeneity found in the work of John Law and and Annemarie Mol.
And because Web 2.0 relies on software, I also turned to software studies to help understand the underlying digital and material layers of Web 2.0. In particular, I turned to analysis of software engineering as a practice, especially the specific ideas of abstraction in software engineering.
Together, the above gave me conceptual tools to decompose Web 2.0 -- what I now would call "corporate social media" -- and engage in a critical approach to technology, using concepts such as labor, value, exploitation, abstraction, and engineering.
The Point is to Change It
But, taking a cue from Andrew Feenberg, it is not simply enough to decompose the object with concepts.
As I write elsewhere (basically paraphrasing Feenberg), "Rather than start with an ideal and bemoaning a world that doesn\'t live up to it, critical theory seeks out contradictions within the objects it encounters. These fissures provide us with tangible ways forward, new possibilities that are not simply abstract, timeless ethical ideals."
Again: this is the other lesson I received from my time at Mason. The point is to change it.
But how could I help change it? I was an English major. Particularly back during my PhD studies, I was not skilled in coding. I was not (and largely still am not) "technical."
But I could look for people -- activists, technologists -- who were challenging the rising corporate domination of the internet.
Part 2: Seeking Critical Reverse Engineers (2008 -- 2014)
My PhD studies led me to the study of people I call "critical reverse engineers," activists who are taking apart the technologies we face, learning how they work, and building better systems.
First, I'll say a bit more about how I'm thinking about critical reverse engineering. Examining the technical literature on reverse engineering, I argue that a critical form of reverse engineering involves the four following orientations:
- Pragmatic
- Genealogical
- Legal
- Normative
The Pragmatic Orientation
Reverse engineers do not imagine an ideal technology. Instead, they start with existing technical objects, taking them apart to see how they have been constructed.

A scene from the AMC show Halt and Catch Fire illustrates this. A two-person team set out to make a new computer called The Giant. Instead of building the ideal machine, they simply reverse-engineered the IBM PC to make a PC clone.
As that scene illustrates, a great deal of this process entails the discovery of \'facts\' discerned through thick, close, detailed empirical analysis of technical objects. How does the technology work? What is it comprised of? Who built it? What might their intentions have been? What can we do with it?
Genealogical
Drawing on Foucauldian thinking, particularly as interpreted by Colin Koopman, I argue that there is a genealogical aspect to reverse engineering.
That is, "reverse engineering" is "forward engineering" in reverse. Engineering typically is a process of developing abstract requirements, then specification documents, and then the specifications are implemented in material.
Reverse engineering starts with the implemented object and then moves backward towards abstract conceptions that may have preceded.
In addition, a reverse engineer engages in what Foucault might call the "gray, meticulous, and patiently documentary" work of poring through comments in code, scrounging for specification documents, or studying the discourses of the organization that created the object under scrutiny.
Legal
The familiar caveat: I am not a lawyer!
But, according to legal scholars who look at reverse engineering -- particularly Pamela Samuelson -- reverse engineering has a tradition of legal protections in contexts such as the United States and the European Union. In traditional manufacturing, U.S. courts have held that the sale of an object is akin to its publication, and thus the legal owner of any object is free to take it apart, study it, and even produce a copy of it for sale.
This situation is a bit more complex with software. Lines of code are protected by copyright; I cannot copy lines of code from a copyrighted program into a new program. But in terms of the functional side, unless it has been protected by a patent, we are free to replicate the functionality of existing software. And in order to do that, we are in fact allowed to open up, probe, test, and disassemble software -- even to make copies of it in the process.
Normative
However, none of the above is necessarily critical. Someone can reverse engineer a technology merely to make a competing product.
To become "critical reverse engineering," we need a critical, normative approach -- we need ethics. That is, we disassemble technical artifacts, produce knowledge from that disassembly, and construct new artifacts that further efforts towards economic and social justice.
So I have been seeking activists engaged in critical reverse engineering of corporate social media -- people who are pragmatic in their relation to technology, use genealogical thinking, exercise their rights to reverse engineer, and do so to make a better world.
Part 3: Adventures in Alternative Social Media (2010 -- 2016)
Seeking out critical reverse engineers of corporate social media set me off on adventures in alternative social media in the years 2010-2016.
Most of the alternatives I studied were Twitter alternatives, such as GNU social and Twister.
GNU social is a microblogging system that is free to download, install, and run. It was was developed by Free Software activists who want to eliminate proprietary software. It is federated (more on this in a bit).
Twister was a fascinating case -- made by Miguel Freitas, a Brazilian software engineer who wanted to provide protesters with censorship-resistant microblogging. He developed a peer-to-peer version of Twitter using both blockchain and bittorrent-style technologies.
I also studied Facebook alternatives, such as diaspora. diaspora was inspired by a presentation from law professor Eben Moglen to a bunch of NYU students in 2010 -- so keep this in mind as you present your research -- technologists may be listening!
And my work even took me onto the dark web -- networks where both readers and producers of websites are anonymized. I studied several dark web social networking systems, where people relied on pseudonyms to engage in social media activities. Many of these systems run on the anonymizing Tor network, but I found examples on I2P and Freenet, as well. Indeed, this work led me to write a book about the dark web.
So, how are these critical reverse engineering projects? Let's go back to the four orientations. These projects are
- Pragmatic: They very often emulate Twitter, since Twitter's functionality is decidedly recognizable as social media but is relatively simple to implement.
- Genealogical: Not only do they examine corporate social media and work back towards the original requirements, they also tend to be built in reaction to the constant changes made to corporate social media
- Legal: They rely on the rights of reverse engineering. Freitas in particular talked to me about clean-room requirements engineering.
- Normative: All of these projects make claims to being more ethical than corporate social media for a variety of reasons.
Critiques of their normative stances
However, I began to notice some shortcomings in that last, normative aspect.
One major reason the activists develop these systems is to shun surveillance capitalism. That's obviously hugely important.
But the overarching philosophy of many of these projects is a very particular version of "freedom" that results in less just outcomes.
As I mention above, GNU social was developed by the Free Software Foundation, which touts Free Software and the "Four Freedoms." These relate in part to freedom of speech, particularly in the face of government restrictions. Along for ride are discourses about openness and cyberlibertarian governance.
This program is extremely individual-centric. Taken to its extreme, it is about the eradication of the network in favor of the completely sovereign individual. The desire seems to be an unfettered subject capable of wielding technology to openly speaking to anyone, anywhere.
Or, as Andrew Ross says in a critique of free software, "Voices proclaiming freedom in every direction, but justice in none." (I'm taking him a bit out of context, but I think it's fair.)
There are many consequences of this freedom myopia.
One consequence of this is that it raises the specter of what the philosopher Herbert Marcuse called "repressive tolerance," where the speech of the marginalized is eradicated through being made equal to the speech of the dominant.

While Marcuse supplies good examples from the 1960s, I explain repressive tolerance to students using the example of the utterance "Blue Lives Matter" -- a means to eradicate the Black Lives Matter movement by placing those already in power on an equal footing to Black victims of police violence.
We saw this play out in the US and elsewhere in the form of the Alt-Right -- Adrienne Massanari has done excellent work linking Gamergate, Silicon Valley ideologies, and rising fascism in the USA. The desire of repressive tolerance is to eradicate the presence of women, gender minorities, or racialized minorities from technical, leisure, and political spaces by maintaining the status quo.
We can also see repressive tolerance at work in the validation of the internet Edgelord -- a phenomenon best explored by Whitney Phillips.
We saw the Gamergate and alt-right movements gain a great deal of traction on Twitter, but the fact is that they have also had a dominant presence on alternative social media, as well, particularly those that have a sociotechnical imaginary of freedom and openness.
The brute fact is, it became increasingly difficult for me to find daylight between many of the alternative projects and Twitter during Gamergate. "Alternative" began to seem, in many ways, to not be very alternative.
That brings me to the present.
Part 4: New Critical Reverse Engineers on the Fediverse (2017 -- Present)
The object spoke again, saying things I was unable to hear when I started my career. I needed to seek new critical reverse engineers.
And that I needed to do the reading in Black philosophy, feminist theory, and queer media studies: authors like Myisha Cherry, André Brock, Catherine Knight Steele, Avery Dame-Griff.
It will take a new wave of critical reverse engineers to reveal how contemporary alternative social media can shed repressive tolerance.
The struggle for the fediverse
This is, in large part, the focus of my current book, which examines Mastodon and the Fediverse.
Because the fediverse includes a wide range of technologies, I focus on Mastodon, a microblogging software package that can be installed and run on modern web servers.
Mastodon provides a window not only into software engineering, but also social and political interventions -- particularly from marginalized critical reverse engineers -- in alternative social media.
From OStatus to ActivityPub
When many people speak about Mastodon, they often place it relation to Twitter. This predates the Musk takeover of Twitter, but it has certainly been amplified since then.
Mastodon appears to be an example of critical reverse engineering of Twitter, and was hailed from its earliest days as such. "Twitter without the Nazis" was a common descriptor.
But as I show in my book, Mastodon's founder, Eugen Rochko, actually meant to critically reverse engineer another alternative, GNU social, in 2016. Mastodon was meant to be an alternative to an alternative. And this brought it into conflict with ideologies of freedom and openness -- the ideologies of repressive tolerance.
Mastodon servers were initially able to communicate with GNU social over a protocol called OStatus. OStatus was a very Web 2.0 technology -- it was about openness, the idea that all of us should participate openly in discussion.
One goal among Mastodon's developers was to provide safety tools to protect marginalized folks, particularly queer and trans folks, allowing for users to address their posts to particular, limited audiences and have more control over who could reply.
These were features not available in GNU social (or, for that matter, Twitter).
However, this grated against the everything-must-be-open-and-free ethos of GNU social.
I won't go into too much detail here, but one major issue was privacy violations on the part of GNU social users, who would publicly expose private posts from queer and trans Mastodon users in the name of "openness" and "freedom."
Fortunately, the ActivityPub protocol was being developed in 2016-2017, and it had more robust privacy capacities. Four of the five authors self-identify as queer, which might explain the new protocol's affordances, including the use of post addressing as a means to protect people.
Mastodon adopted ActivityPub, denying the repressive forms of openness of OStatus in favor of safety for marginalized people.
Codes of Conduct
Another anti-repressive tolerance move: the inclusion of codes of conduct, as advocated for by activists such as Coraline Ada Ehmke. Codes of conduct are important in Mastodon's history.
Ehmke's work reflects feminist/trans activism in tech -- the struggle against meritocracy. This struggle emerged from projects like the Geek Feminism wiki, which documented misogyny and transphobia at tech conventions.
These practices were cited as the reason why technology -- particularly FOSS technology -- has had a significant lack of contributions from women and racialized minorities.
Ehmke and her allies laid the feet of such behavior at the ideology of meritocracy in tech, where, as Eric Raymond argued, the only thing that matters is great code. Implicitly, being a sexual abuser or racist is ok so long as you can code.
Other scholars and activists have pointed to "pushyocracy," where it's not about great code but about who can shout the loudest, as a reason why marginalized people avoided getting involved in the tech indstury. (Linus Torvalds has been a key example of this, though he has since sought forgiveness.)
Instead of meritocracy at tech conventions, Ehmke and her allies have argued for Codes of Conduct, which have been largely adopted by both tech conventions and free and open source projects.
As I show in the book, these Codes have also been adopted by many Mastodon servers. I argue these act as fundamental diplomatic documents in noncentralized social media: codes of conduct help structure relations on the network. The active association among instances who share ethical values indicates an ethical consensus is emerging across the network including values of anti-racism and anti-transphobia.
#Fediblock and Blocklists
While much of the code of conduct discussion is about shared ethical values, what about times when fediverse instances violate these agreements? Another anti-repressive tolerance move can be found among those who advocate severing connections.
Here I turn to another critical reverse engineer, Ro, founder of an early Mastodon instance called "Playvicious.social."
Playvicious was likely the first Black-run instance on Mastodon. But Ro shut it down in 2020, citing racist harassment of the moderators. You can read about it on his blog -- but I warn you, it's heavy.
The Playvicious episode -- and many others -- reflected what Jonathan Flowers would later call "the whiteness of Mastodon," the deeply embedded practices of whiteness that not only include overt racism, but the subtle forms philosopher Myisha Cherry calls "white skepticism" and "white empathy."
But, to quote Flowers, Black critical reverse engineers continue to contribute in spite of whiteness. In Ro's case, he returned to the network with a new project, a shared blocklist called The Bad Space.
Blocklists are now an emergent governance and moderation tool on the fediverse, enabling independent instances to import lists of known bad actors and prevent them from interacting with instance members. Ro's Bad Space isn't the only project, though it is one that seems to attract the most criticism -- recapitulating the Playvicious episode in a new form.
There's another critical reverse engineer to cite here. Ro took inspiration for his blocklist from former Playvicious moderator Marcia X. Like many Black feminists, Marcia has contributed to the network, co-creating a hashtag, #fediblock, for public discussions over how to block racist instances and accounts on the network.
I've put their work into practice. The work of Black critical reverse engineers has aided me directly -- I now help run AoIR.social, the Mastodon instance for the Association of Internet Researchers, and we rely on blocklists and #fediblock to prevent racists and transphobes from interacting with our members.
Towards the Covenantal Fediverse
Taken as a whole, these new critical reverse engineers have helped bring about a new form of alternative social media.
It is a form a colleague and I have called "the covenantal fediverse," a non-centralized, large network of small communities that associate through shared ethical values.
Here is a new normative critical reverse engineering of corporate social media. Returning to the four orientations of critical reverse engineering, let's turn back to the normative orientation.
The normative aspect of Mastodon and the covenantal fediverse relates to previous alternative social media. In some ways, the fediverse continues older normative practices. It inherits the anti-surveillance capitalism aspects of previous alternatives, of course. Most of the fediverse operates on a non-capitalist, mutual aid economy. Much of it avoids behavioral advertising.
However, the older cyberlibertarianism is replaced -- often in a messy and uneven way -- with freedom of association. By accident or design, the Instance is a powerful unit. I would suggest that our understanding of the fediverse needs to account more heavily for instances-as-communities instead of the individual user (as has been privileged in cyberlibertarian thinking).
Conclusion: Will this survive?
Now I have traced a new form of critical reverse engineering, one operating on both corporate social media and previous alternative social media. I believe it is best existing path away from corporate social media.
And yet, while millions of people took up Mastodon after Musk's purchase of Twitter, billions remain on corporate social media.
To return to where I started, even critical media organizations that speak of non-corporate media continue to use corporate social media!
We might ask "can this platform survive?" as several colleagues from American University and I do in a forthcoming paper in the International Journal of Communication.
And my answer is: I don't know. Many alternative projects have failed.
But let's again listen to the object. Alternative social media speaks of hope, even in the face of failure (however we define that idea!). To use a term from speculative fiction, alternative social media speaks of porvir otimista.
Don't despair in the face of the sociotechnical systems you confront. Instead, critically reverse engineer them.


Comments
For each of these posts, I will also post to Mastodon. If you have a fediverse account and reply to my Mastodon post, that shows up as a comment on this blog unless you change your privacy settings to followers-only or DM. Content warnings will work. You can delete your comment by deleting it through Mastodon.
Don't have a fediverse account and you want one? Ask me how! robertwgehl AT protonmail . com
Reply through Fediverse